Caesar Cipher Tool
Shift Visualization
Secure Encryption
Protect your messages with the classic Caesar cipher encryption method, a foundational technique in cryptography.
Easy Decryption
Decrypt messages that were encrypted using the Caesar cipher with our intuitive decryption tool.
Enterprise Security
Built with enterprise-grade security standards, including secure processing and comprehensive audit logging.
Advanced Analytics
Perform brute force analysis and frequency studies to test the strength of your encrypted messages.
Visual Learning
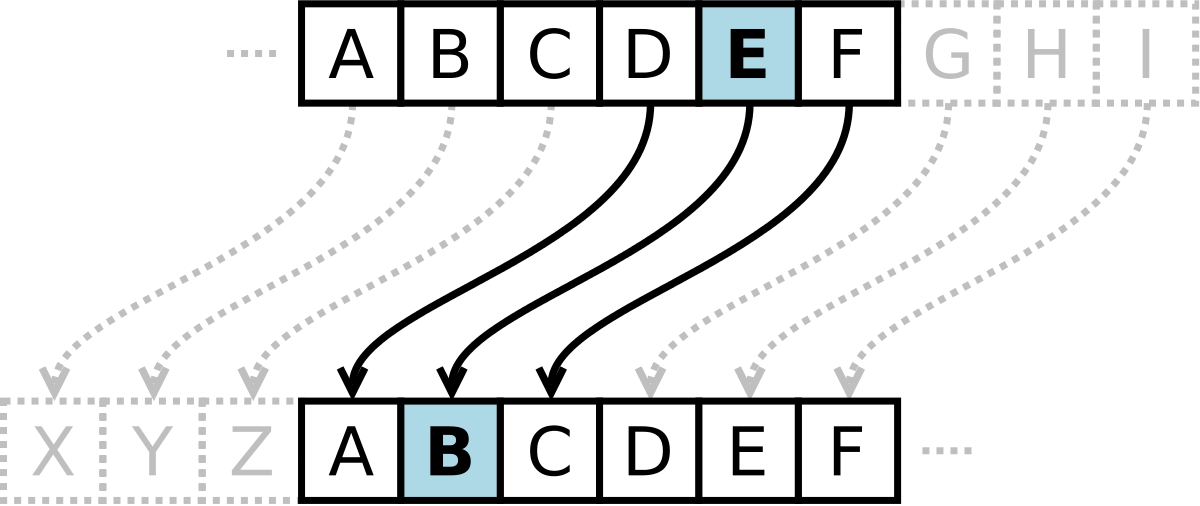
Understand how the Caesar cipher works with our interactive visualization of the alphabet shift.
Cross-Platform
Access our enterprise encryption tool from any device with a modern web browser. No installation required.
About Caesar Cipher
The Caesar cipher, named after Julius Caesar who used it around 58-50 BCE during the Gallic Wars, is one of the simplest and most widely known encryption techniques in cryptography. Caesar employed this method with a shift of 3 to protect his military communications with generals. The cipher works by shifting each letter in the alphabet by a fixed number of positions - for example, with a shift of 3, 'A' becomes 'D', 'B' becomes 'E', and so on. When the shift reaches the end of the alphabet, it wraps around to the beginning using modular arithmetic.
While historically significant as one of the earliest documented encryption methods, the Caesar cipher is extremely vulnerable by modern security standards. With only 25 possible keys (shifts 1-25), it can be easily broken through brute force attacks or frequency analysis. Today, it serves primarily educational purposes, helping students understand basic cryptographic concepts, and is used in puzzles, games, and simple text obfuscation. The cipher's simplicity makes it an excellent introduction to the world of cryptography, demonstrating fundamental principles that evolved into more sophisticated encryption methods like the Vigenère cipher and modern cryptographic algorithms.
How to Use
- Enter Your Message: Type or paste the text you want to encrypt or decrypt in the message field.
- Set Shift Value: Choose a shift value between 1 and 25.
- Select Operation: Choose whether you want to encrypt, decrypt, or perform brute force analysis.
- Process: Click the "Process" button to perform the operation. The page will reload with the result.
- View Result: The result will appear in the result box below.